Entity Set in DBMS-
Before you go through this article, make sure that you have gone through the previous article on Introduction to ER Diagrams.
| An entity set is a set of same type of entities. |
An entity refers to any object having-
- Either a physical existence such as a particular person, office, house or car.
- Or a conceptual existence such as a school, a university, a company or a job.
In ER diagram,
- Attributes are associated with an entity set.
- Attributes describe the properties of entities in the entity set.
- Based on the values of certain attributes, an entity can be identified uniquely.
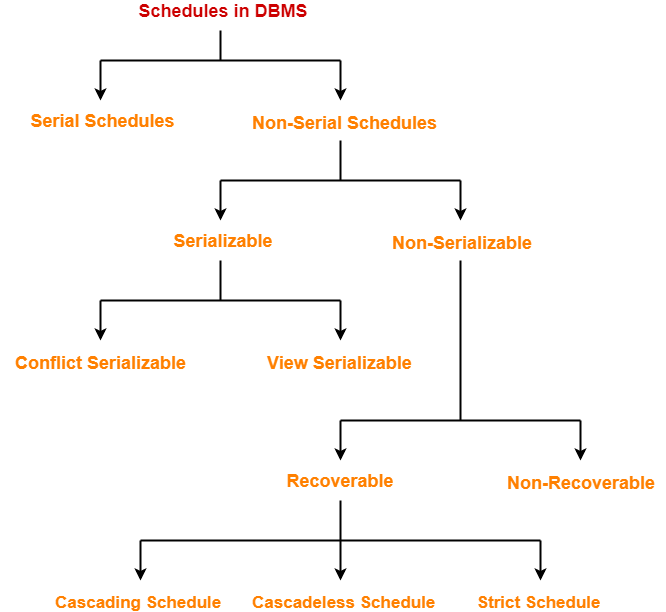
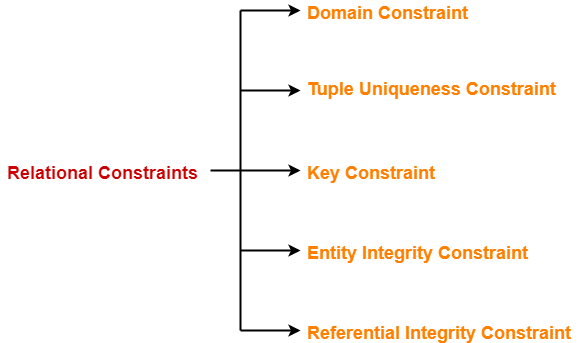
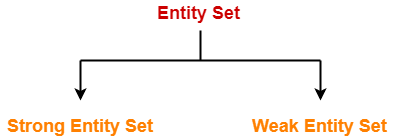
Types of Entity Sets-
An entity set may be of the following two types-
- Strong entity set
- Weak entity set
1. Strong Entity Set-
- A strong entity set is an entity set that contains sufficient attributes to uniquely identify all its entities.
- In other words, a primary key exists for a strong entity set.
- Primary key of a strong entity set is represented by underlining it.
Symbols Used-
- A single rectangle is used for representing a strong entity set.
- A diamond symbol is used for representing the relationship that exists between two strong entity sets.
- A single line is used for representing the connection of the strong entity set with the relationship set.
- A double line is used for representing the total participation of an entity set with the relationship set.
- Total participation may or may not exist in the relationship.
Example-
Consider the following ER diagram-
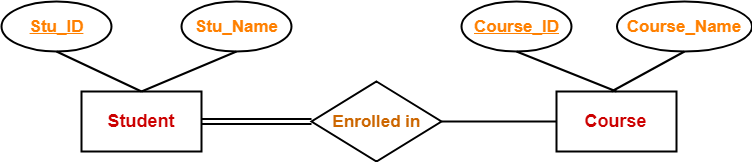
In this ER diagram,
- Two strong entity sets “Student” and “Course” are related to each other.
- Student ID and Student name are the attributes of entity set “Student”.
- Student ID is the primary key using which any student can be identified uniquely.
- Course ID and Course name are the attributes of entity set “Course”.
- Course ID is the primary key using which any course can be identified uniquely.
- Double line between Student and relationship set signifies total participation.
- It suggests that each student must be enrolled in at least one course.
- Single line between Course and relationship set signifies partial participation.
- It suggests that there might exist some courses for which no enrollments are made.
2. Weak Entity Set-
- A weak entity set is an entity set that does not contain sufficient attributes to uniquely identify its entities.
- In other words, a primary key does not exist for a weak entity set.
- However, it contains a partial key called as a discriminator.
- Discriminator can identify a group of entities from the entity set.
- Discriminator is represented by underlining with a dashed line.
NOTE-
- The combination of discriminator and primary key of the strong entity set makes it possible to uniquely identify all entities of the weak entity set.
- Thus, this combination serves as a primary key for the weak entity set.
- Clearly, this primary key is not formed by the weak entity set completely.

Symbols Used-
- A double rectangle is used for representing a weak entity set.
- A double diamond symbol is used for representing the relationship that exists between the strong and weak entity sets and this relationship is known as identifying relationship.
- A double line is used for representing the connection of the weak entity set with the relationship set.
- Total participation always exists in the identifying relationship.
Example-
Consider the following ER diagram-
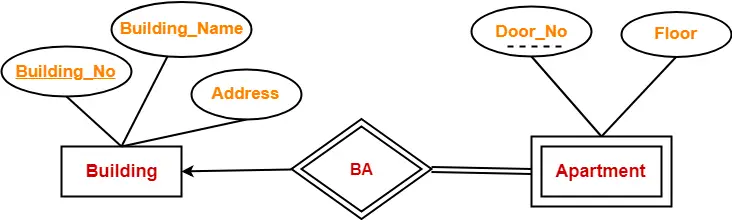
In this ER diagram,
- One strong entity set “Building” and one weak entity set “Apartment” are related to each other.
- Strong entity set “Building” has building number as its primary key.
- Door number is the discriminator of the weak entity set “Apartment”.
- This is because door number alone can not identify an apartment uniquely as there may be several other buildings having the same door number.
- Double line between Apartment and relationship set signifies total participation.
- It suggests that each apartment must be present in at least one building.
- Single line between Building and relationship set signifies partial participation.
- It suggests that there might exist some buildings which has no apartment.
To uniquely identify any apartment,
- First, building number is required to identify the particular building.
- Secondly, door number of the apartment is required to uniquely identify the apartment.
Thus,
Primary key of Apartment
= Primary key of Building + Its own discriminator
= Building number + Door number
Differences between Strong entity set and Weak entity set-
| Strong entity set | Weak entity set |
| A single rectangle is used for the representation of a strong entity set. | A double rectangle is used for the representation of a weak entity set. |
| It contains sufficient attributes to form its primary key. | It does not contain sufficient attributes to form its primary key. |
| A diamond symbol is used for the representation of the relationship that exists between the two strong entity sets. | A double diamond symbol is used for the representation of the identifying relationship that exists between the strong and weak entity set. |
| A single line is used for the representation of the connection between the strong entity set and the relationship. | A double line is used for the representation of the connection between the weak entity set and the relationship set. |
| Total participation may or may not exist in the relationship. | Total participation always exists in the identifying relationship. |
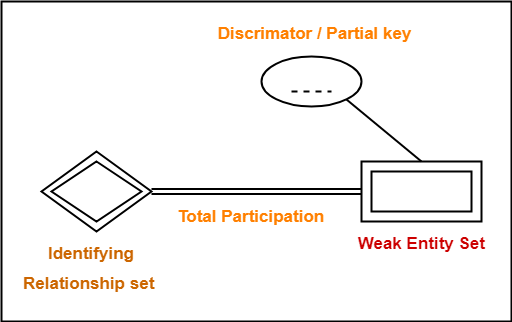
Important Note-
In ER diagram, weak entity set is always present in total participation with the identifying relationship set.
So, we always have the picture like shown here-
Next Article- Relationship Sets in DBMS
Get more notes and other study material of Database Management System (DBMS).
Watch video lectures by visiting our YouTube channel LearnVidFun.