Cryptography in Network Security-
In network security,
- Cryptography is a method of storing and transmitting data in a particular form.
- It ensures that only the person for whom the message is intended can read the message.
The message exchange using cryptography involves the following steps-
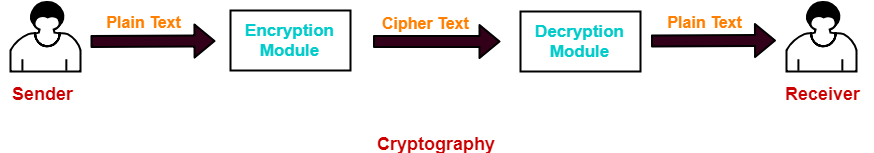
Step-01:
At sender side,
- Using an encryption algorithm, the message is converted into an unreadable form.
- The message in unreadable form is called as cipher text.
Step-02:
- The cipher text is sent to the receiver over the communication channel.
- Since the message is encrypted, the attackers can not read the message.
Step-03:
At receiver side,
- Using a decryption algorithm, the message is again converted into the readable form.
- Then, receiver can read the message.
Cryptography Techniques-
Cryptography techniques may be classified as-
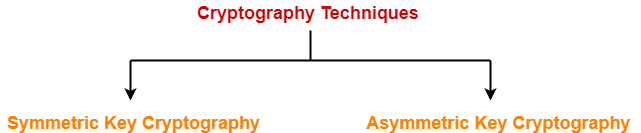
- Symmetric Key Cryptography
- Asymmetric Key Cryptography
In this article, we will discuss about symmetric key cryptography.
Symmetric Key Cryptography-
In this technique,
- Both sender and receiver uses a common key to encrypt and decrypt the message.
- This secret key is known only to the sender and to the receiver.
- It is also called as secret key cryptography.
Working-
The message exchange using symmetric key cryptography involves the following steps-
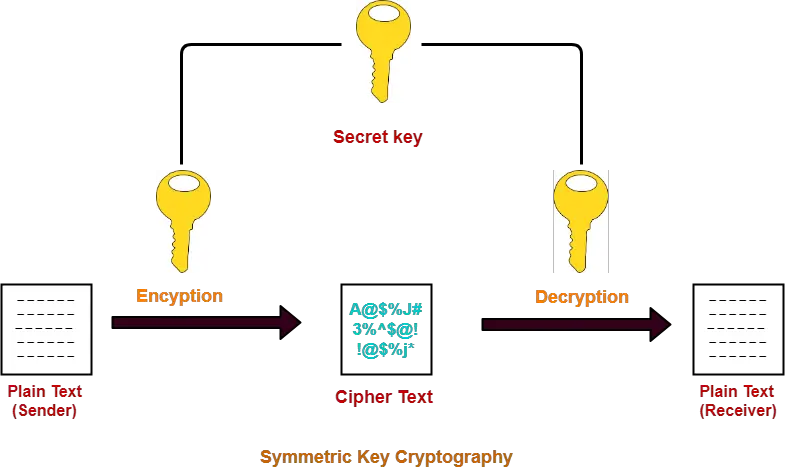
- Before starting the communication, sender and receiver shares the secret key.
- This secret key is shared through some external means.
- At sender side, sender encrypts the message using his copy of the key.
- The cipher text is then sent to the receiver over the communication channel.
- At receiver side, receiver decrypts the cipher text using his copy of the key.
- After decryption, the message converts back into readable format.
Symmetric Encryption Algorithms-
Some of the encryption algorithms that use symmetric key are-
- Advanced Encryption Standard (AES)
- Data Encryption Standard (DES)
Advantages-
The advantages of symmetric key algorithms are-
- They are efficient.
- They take less time to encrypt and decrypt the message.
Disadvantages-
Point-01:
| The number of keys required is very large. |
In symmetric key cryptography,
- Each pair of users require a unique secret key.
- If N people in the world wants to use this technique, then there needs to be N(N-1) / 2 secret keys.
- For 1 million people to communicate, a half billion secret keys would be needed.
How N(N-1)/2 Keys Will Be Required?
|
Point-02:
- Sharing the secret key between the sender and receiver is an important issue.
- While sharing the key, attackers might intrude.
|
To overcome this disadvantage, Diffie Hellman Key Exchange Algorithm is used for exchanging the secret key. |
Important Points-
Point-01:
In symmetric key cryptography,
- Both sender and receiver uses the same key.
- Sender encrypts the message using his copy of the key.
- Receiver decrypts the message using his copy of the key.
- The key must not be known to anyone else other than sender and receiver.
- If the secret key is known to any intruder, he could decrypt the message.
Point-02:
- This cryptography technique is called as symmetric key cryptography.
- It is because both sender and receiver use the same key on their sides.
Point-03:
- This cryptography technique is called as secret key cryptography.
- It is because the key has to be kept secret between the sender and receiver.
To gain better understanding about Symmetric Key Cryptography,
Next Article- Asymmetric Key Cryptography | RSA Algorithm
Get more notes and other study material of Computer Networks.
Watch video lectures by visiting our YouTube channel LearnVidFun.