Computer Networks By Tanenbaum
This article reviews the book “Computer Networks” by Andrew S. Tanenbaum and David J. Wetherall.
The article covers-
- Special features of book
- Analysis of Content
- Analysis of Exercises
- Necessary Instructions
- Conclusion
 Why Should Be Read?
Why Should Be Read?
Special Features of Book-
The special features of this book are-
- It contains the most well-balanced text for this subject.
- It covers the concepts in detail without getting verbose.
- It contains clear and concise diagrams and tables.
- It is a good choice for beginners and intermediate level students.
- The chapters covering Data Link layer and Network layer are explained in great detail.
- No other text book has as clear explanation for Transport layer as this book has.
- Exercise questions are numerical as well as conceptual in nature.
- The difficulty level of exercise questions is at par with the level of questions asked in GATE.
Analysis of Content-
The following table analyzes sections of the book that are relevant for GATE-
| Chapter No. | GATE Relevant Sections | GATE Topics Covered |
| 1 | 1.4 | Reference Models (OSI and TCP/IP) |
| 2 | 2.5.1 | Transmission Encoding (NRZ, Manchester etc) |
| 2.6.5 | Switching (Circuit and Packet) | |
| 3 | 3.1 | Basics of Data Link Layer |
| 3.2 | Error Detection and Correction | |
| 3.3.2 | Flow Control
(Stop and Wait, Sliding Window Techniques) |
|
| 3.4 | ||
| 4 | 4.2.1 | Multiple Access Protocols
(Aloha and CSMA) |
| 4.2.2 | ||
| 4.3 | Ethernet | |
| 4.4 | WiFi | |
| 4.8 | Networking Devices
(Bridge, Hub, Switch etc) |
|
| 5 | 5.1 | Network Layer Introduction |
| 5.2.1 to 5.2.5 | Routing (Distance Vector and Link State Routing) | |
| 5.4.2 | Traffic Shaping (Leaky and Token Bucket) | |
| 5.6.1 to 5.6.3 | Internet Protocol (IPv4 and IPv6) | |
| 6 | 6.1.3 | Sockets |
| 6.4.1 | User Datagram Protocol (UDP) | |
| 6.5.1 to 6.5.10 | Transmission Control Protocol (TCP) | |
| 7 | 7.1 to 7.3 | Application Layer Protocols |
| 8 | 8.3 | Public Key Algorithms |
| 8.4.2 | Digital Signatures and Message Digests | |
| 8.4.3 | ||
| 8.5.1 | Digital Certificates | |
| 8.6.2 | Firewalls | |
| 8.7.2 | Diffie-Hellman Key Exchange |
Covering Only These Sections Is Enough
Analysis of Exercises-
The following table analyzes exercises of the book that are relevant for GATE-
| Chapter No. | Question No. |
| 1 | 15, 16, 22, 27, 28 |
| 2 | 37, 38, 39 |
| 3 | 1, 2, 6, 8, 11, 13, 15, 16, 18, 20, 22, 32, 33, 35 |
| 4 | 2, 4, 6, 10, 13, 15, 16, 38 |
| 5 | 6, 7, 16, 18, 19, 23, 24, 25, 26, 28, 30, 31, 33, 37, 40 |
| 6 | 7, 9, 22, 26, 28, 30, 31, 32, 33, 34, 36, 42, 43 |
| 7 | 4, 20, 42 |
| 8 | 17, 18, 22, 32, 33 |
Practicing Only These Exercises Is Enough
Necessary Instructions-
Keep the following instructions in mind while reading the book-
- Competitive exams focus mainly on numerical questions in this subject.
- Make sure to solve the exercises of relevant chapters.
- Keep making notes while reading the relevant sections.
- The well-illustrated diagrams and tables can directly be a part of your short notes.
- Be thorough with the understanding of header formats and frame formats of various protocols.
- Most of the questions require knowing the concepts of TCP, UDP, IP etc in detail.
- The book covers all the topics of GATE syllabus.
Conclusion-
- The book balances the theoretical and practical aspects of the subject pretty well.
- The numerical exercises are quite good and strongly recommended for practice.
| THIS BOOK IS SELF-SUFFICIENT FOR GATE EXAM. |
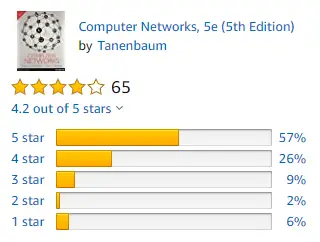
Amazon Rating
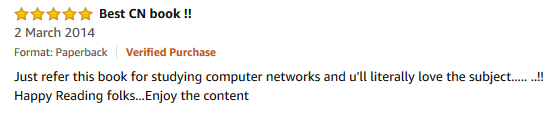
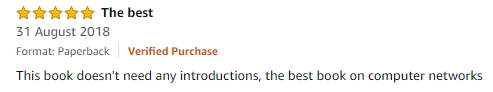
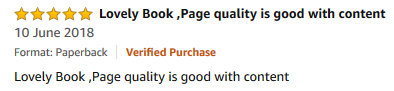
Student’s Reviews-



Other Recommended Books-
Data Communications And Networking By Fourozan-
Computer Networking By Kurose And Ross-



