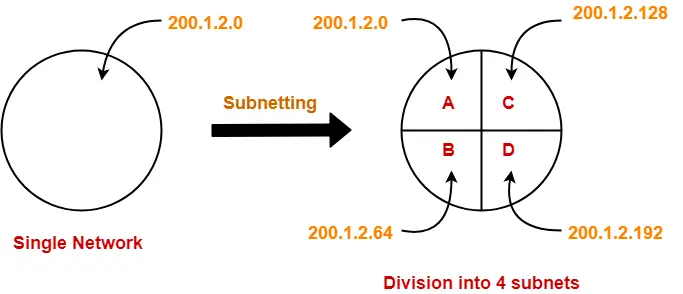
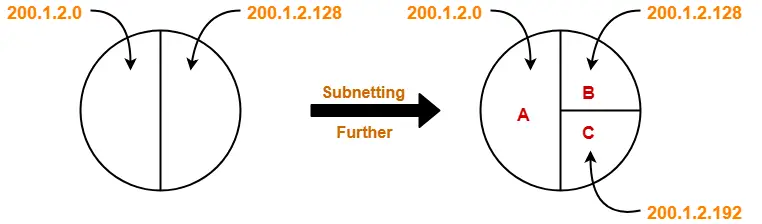
IP Addressing-
There are two systems in which IP Addresses are classified-
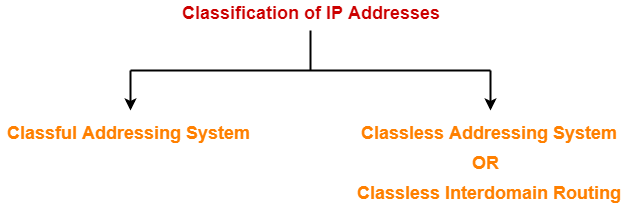
- Classful Addressing System
- Classless Addressing System
In this article, we will discuss about Classless Addressing System.
Learn about Classful Addressing System.
Classless Addressing-
- Classless Addressing is an improved IP Addressing system.
- It makes the allocation of IP Addresses more efficient.
- It replaces the older classful addressing system based on classes.
- It is also known as Classless Inter Domain Routing (CIDR).
CIDR Block-
When a user asks for specific number of IP Addresses,
- CIDR dynamically assigns a block of IP Addresses based on certain rules.
- This block contains the required number of IP Addresses as demanded by the user.
- This block of IP Addresses is called as a CIDR block.
Rules For Creating CIDR Block-
A CIDR block is created based on the following 3 rules-
Rule-01:
- All the IP Addresses in the CIDR block must be contiguous.
Rule-02:
- The size of the block must be presentable as power of 2.
- Size of the block is the total number of IP Addresses contained in the block.
- Size of any CIDR block will always be in the form 21, 22, 23, 24, 25 and so on.
Rule-03:
- First IP Address of the block must be divisible by the size of the block.
REMEMBER
If any binary pattern consisting of (m + n) bits is divided by 2n, then-
So, any binary pattern is divisible by 2n, if and only if its least significant n bits are 0.
Examples-
Consider a binary pattern- 01100100.00000001.00000010.01000000 (represented as 100.1.2.64)
|
CIDR Notation-
CIDR IP Addresses look like-
a.b.c.d / n
- They end with a slash followed by a number called as IP network prefix.
- IP network prefix tells the number of bits used for the identification of network.
- Remaining bits are used for the identification of hosts in the network.
Example-
An example of CIDR IP Address is-
182.0.1.2 / 28
It suggests-
- 28 bits are used for the identification of network.
- Remaining 4 bits are used for the identification of hosts in the network.
PRACTICE PROBLEMS BASED ON CLASSLESS INTER DOMAIN ROUTING-
Problem-01:
Given the CIDR representation 20.10.30.35 / 27. Find the range of IP Addresses in the CIDR block.
Solution-
Given CIDR representation is 20.10.30.35 / 27.
It suggests-
- 27 bits are used for the identification of network.
- Remaining 5 bits are used for the identification of hosts in the network.
Given CIDR IP Address may be represented as-
00010100.00001010.00011110.00100011 / 27
So,
- First IP Address = 00010100.00001010.00011110.00100000 = 20.10.30.32
- Last IP Address = 00010100.00001010.00011110.00111111 = 20.10.30.63
Thus, Range of IP Addresses = [ 20.10.30.32 , 20.10.30.63]
Problem-02:
Given the CIDR representation 100.1.2.35 / 20. Find the range of IP Addresses in the CIDR block.
Solution-
Given CIDR representation is 100.1.2.35 / 20.
It suggests-
- 20 bits are used for the identification of network.
- Remaining 12 bits are used for the identification of hosts in the network.
Given CIDR IP Address may be represented as-
01100100.00000001.00000010.00100011 / 20
So,
- First IP Address = 01100100.00000001.00000000.00000000 = 100.1.0.0
- Last IP Address = 01100100.00000001.00001111.11111111 = 100.1.15.255
Thus, Range of IP Addresses = [ 100.1.0.0 , 100.1.15.255]
Problem-03:
Consider a block of IP Addresses ranging from 100.1.2.32 to 100.1.2.47.
- Is it a CIDR block?
- If yes, give the CIDR representation.
Solution-
For any given block to be a CIDR block, 3 rules must be satisfied-
Rule-01:
- According to Rule-01, all the IP Addresses must be contiguous.
- Clearly, all the given IP Addresses are contiguous.
- So, Rule-01 is satisfied.
Rule-02:
- According to Rule-02, size of the block must be presentable as 2n.
- Number of IP Addresses in the given block = 47 – 32 + 1 = 16.
- Size of the block = 16 which can be represented as 24.
- So, Rule-02 is satisfied.
Rule-03:
- According to Rule-03, first IP Address must be divisible by size of the block.
- So, 100.1.2.32 must be divisible by 24.
- 100.1.2.32 = 100.1.2.00100000 is divisible by 24 since its 4 least significant bits are zero.
- So, Rule-03 is satisfied.
Since all the rules are satisfied, therefore given block is a CIDR block.
CIDR Representation-
We have-
- Size of the block = Total number of IP Addresses = 24.
- To have 24 total number of IP Addresses, total 4 bits are required in the Host ID part.
- So, Number of bits present in the Network ID part = 32 – 4 = 28.
Thus,
| CIDR Representation = 100.1.2.32 / 28 |
NOTE-
For writing the CIDR representation,
- We can choose to mention any IP Address from the CIDR block.
- The chosen IP Address is followed by a slash and IP network prefix.
- We generally choose to mention the first IP Address.
Problem-04:
Consider a block of IP Addresses ranging from 150.10.20.64 to 150.10.20.127.
- Is it a CIDR block?
- If yes, give the CIDR representation.
Solution-
For any given block to be a CIDR block, 3 rules must be satisfied-
Rule-01:
- According to Rule-01, all the IP Addresses must be contiguous.
- Clearly, all the given IP Addresses are contiguous.
- So, Rule-01 is satisfied.
Rule-02:
- According to Rule-02, size of the block must be presentable as 2n.
- Number of IP Addresses in given block = 127 – 64 + 1 = 64.
- Size of the block = 64 which can be represented as 26.
- So, Rule-02 is satisfied.
Rule-03:
- According to Rule-03, first IP Address must be divisible by size of the block.
- So, 150.10.20.64 must be divisible by 26.
- 150.10.20.64 = 150.10.20.01000000 is divisible by 26 since its 6 least significant bits are zero.
- So, Rule-03 is satisfied.
Since all the rules are satisfied, therefore given block is a CIDR block.
CIDR Representation-
We have-
- Size of the block = Total number of IP Addresses = 26.
- To have 26 total number of IP Addresses, 6 bits are required in the Host ID part.
- So, Number of bits in the Network ID part = 32 – 6 = 26.
Thus,
| CIDR Representation = 150.10.20.64 / 26 |
Problem-05:
Perform CIDR aggregation on the following IP Addresses-
128.56.24.0/24
128.56.25.0/24
128.56.26.0/24
128.56.27.0/24
Solution-
All the 4 given entities represent CIDR block in itself.
We have to now perform the aggregation of these 4 blocks.
Rule-01:
- According to Rule-01, all the IP Addresses must be contiguous.
- Clearly, all the IP Addresses are contiguous.
- So, Rule-01 is satisfied.
Rule-02:
- According to Rule-02, size of the block must be presentable as 2n.
- Total number of IP Addresses = 28 + 28 + 28 + 28 = 22 x 28 = 210.
- So, Rule-02 is satisfied.
Rule-03:
- According to Rule-03, first IP Address must be divisible by size of the block.
- So, 128.56.24.0 must be divisible by 210.
- 128.56.24.0 = 128.56.00011000.00000000 is divisible by 210 since its 10 least significant bits are zero.
- So, Rule-03 is satisfied.
Since all the 3 rules are satisfied, so they can be aggregated.
CIDR Representation-
We have-
- Size of the block = Total number of IP Addresses = 210.
- To have 210 total number of IP Addresses, 10 bits are required in the Host ID part.
- So, Number of bits in the Network ID part = 32 – 10 = 22.
Thus,
| CIDR Representation = 128.56.24.0/22 |
Problem-06:
Perform CIDR aggregation on the following IP Addresses-
200.96.86.0/24
200.96.87.0/24
200.96.88.0/24
200.96.89.0/24
Solution-
All the 4 given entities represent CIDR block in itself.
We have to now perform the aggregation of these 4 blocks.
Rule-01:
- According to Rule-01, all the IP Addresses must be contiguous.
- Clearly, all the IP Addresses are contiguous.
- So, Rule-01 is satisfied.
Rule-02:
- According to Rule-02, size of the block must be presentable as 2n.
- Total number of IP Addresses = 28 + 28 + 28 + 28 = 22 x 28 = 210.
- So, Rule-02 is satisfied.
Rule-03:
- According to Rule-03, first IP Address must be divisible by size of the block.
- So, 200.96.86.0 must be divisible by 210.
- 200.96.86.0 = 200.96.01010110.00000000 is not divisible by 210 since its 10 least significant bits are not zero.
- So, Rule-03 is unsatisfied.
Since all the 3 rules are not satisfied, so they can not be aggregated.
To gain better understanding about Classless Addressing,
Next Article- Subnetting | Examples
Get more notes and other study material of Computer Networks.
Watch video lectures by visiting our YouTube channel LearnVidFun.