Transmission Control Protocol-
Before you go through this article, make sure that you have gone through the previous article on TCP in Networking.
We have discussed-
- Transmission Control Protocol is a transport layer protocol.
- It continuously receives data from the application layer.
- It divides the data into chunks where each chunk is a collection of bytes.
- It then creates TCP segments by adding a TCP header to the data chunks.
- TCP segments are encapsulated in the IP datagram.
| TCP segment = TCP header + Data chunk |
In this article, we will discuss about TCP Header.
TCP Header-
The following diagram represents the TCP header format-
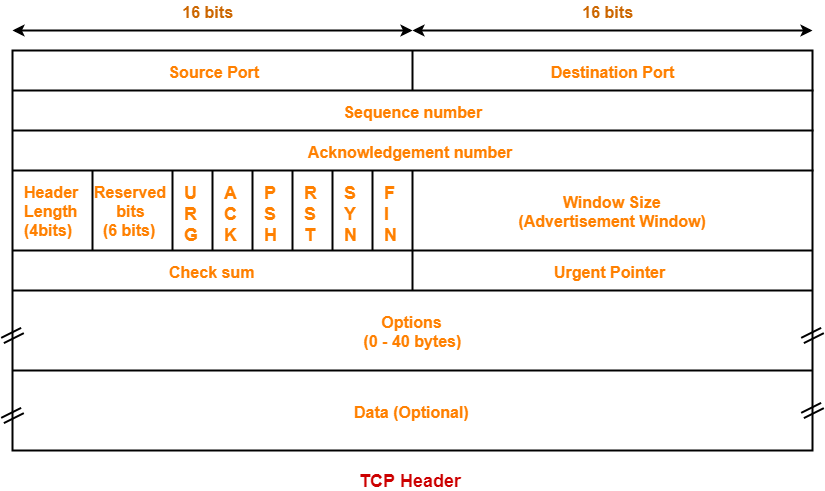
Let us discuss each field of TCP header one by one.
1. Source Port-
- Source Port is a 16 bit field.
- It identifies the port of the sending application.
2. Destination Port-
- Destination Port is a 16 bit field.
- It identifies the port of the receiving application.
NOTE
It is important to note-
- A TCP connection is uniquely identified by using-
Combination of port numbers and IP Addresses of sender and receiver
- IP Addresses indicate which systems are communicating.
- Port numbers indicate which end to end sockets are communicating.
|
3. Sequence Number-
- Sequence number is a 32 bit field.
- TCP assigns a unique sequence number to each byte of data contained in the TCP segment.
- This field contains the sequence number of the first data byte.
4. Acknowledgement Number-
- Acknowledgment number is a 32 bit field.
- It contains sequence number of the data byte that receiver expects to receive next from the sender.
- It is always sequence number of the last received data byte incremented by 1.
5. Header Length-
- Header length is a 4 bit field.
- It contains the length of TCP header.
- It helps in knowing from where the actual data begins.
Minimum and Maximum Header length-
| The length of TCP header always lies in the range-
[20 bytes , 60 bytes]
|
- The initial 5 rows of the TCP header are always used.
- So, minimum length of TCP header = 5 x 4 bytes = 20 bytes.
- The size of the 6th row representing the Options field vary.
- The size of Options field can go up to 40 bytes.
- So, maximum length of TCP header = 20 bytes + 40 bytes = 60 bytes.
Concept of Scaling Factor-
- Header length is a 4 bit field.
- So, the range of decimal values that can be represented is [0, 15].
- But the range of header length is [20, 60].
- So, to represent the header length, we use a scaling factor of 4.
In general,
| Header length = Header length field value x 4 bytes |
Examples-
- If header length field contains decimal value 5 (represented as 0101), then-
Header length = 5 x 4 = 20 bytes
- If header length field contains decimal value 10 (represented as 1010), then-
Header length = 10 x 4 = 40 bytes
- If header length field contains decimal value 15 (represented as 1111), then-
Header length = 15 x 4 = 60 bytes
NOTES
It is important to note-
- Header length and Header length field value are two different things.
- The range of header length field value is always [5, 15].
- The range of header length is always [20, 60].
While solving questions-
- If the given value lies in the range [5, 15] then it must be the header length field value.
- This is because the range of header length is always [20, 60].
|
6. Reserved Bits-
- The 6 bits are reserved.
- These bits are not used.
7. URG Bit-
| URG bit is used to treat certain data on an urgent basis. |
When URG bit is set to 1,
- It indicates the receiver that certain amount of data within the current segment is urgent.
- Urgent data is pointed out by evaluating the urgent pointer field.
- The urgent data has be prioritized.
- Receiver forwards urgent data to the receiving application on a separate channel.
8. ACK Bit-
| ACK bit indicates whether acknowledgement number field is valid or not. |
- When ACK bit is set to 1, it indicates that acknowledgement number contained in the TCP header is valid.
- For all TCP segments except request segment, ACK bit is set to 1.
- Request segment is sent for connection establishment during Three Way Handshake.
9. PSH Bit-
| PSH bit is used to push the entire buffer immediately to the receiving application. |
When PSH bit is set to 1,
- All the segments in the buffer are immediately pushed to the receiving application.
- No wait is done for filling the entire buffer.
- This makes the entire buffer to free up immediately.
NOTE
It is important to note-
- Unlike URG bit, PSH bit does not prioritize the data.
- It just causes all the segments in the buffer to be pushed immediately to the receiving application.
- The same order is maintained in which the segments arrived.
- It is not a good practice to set PSH bit = 1.
- This is because it disrupts the working of receiver’s CPU and forces it to take an action immediately.
|
10. RST Bit-
| RST bit is used to reset the TCP connection. |
When RST bit is set to 1,
- It indicates the receiver to terminate the connection immediately.
- It causes both the sides to release the connection and all its resources abnormally.
- The transfer of data ceases in both the directions.
- It may result in the loss of data that is in transit.
This is used only when-
- There are unrecoverable errors.
- There is no chance of terminating the TCP connection normally.
11. SYN Bit-
| SYN bit is used to synchronize the sequence numbers. |
When SYN bit is set to 1,
- It indicates the receiver that the sequence number contained in the TCP header is the initial sequence number.
- Request segment sent for connection establishment during Three way handshake contains SYN bit set to 1.
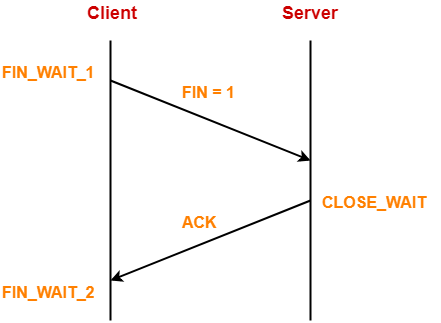
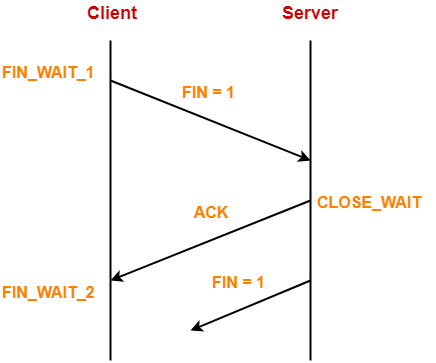
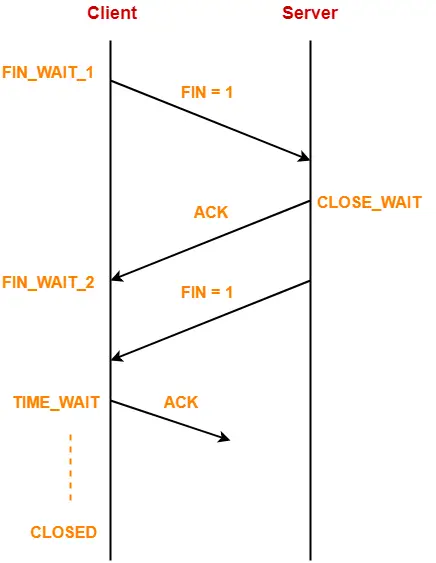
12. FIN Bit-
| FIN bit is used to terminate the TCP connection. |
When FIN bit is set to 1,
- It indicates the receiver that the sender wants to terminate the connection.
- FIN segment sent for TCP Connection Termination contains FIN bit set to 1.
13. Window Size-
- Window size is a 16 bit field.
- It contains the size of the receiving window of the sender.
- It advertises how much data (in bytes) the sender can receive without acknowledgement.
- Thus, window size is used for Flow Control.
NOTE
It is important to note-
- The window size changes dynamically during data transmission.
- It usually increases during TCP transmission up to a point where congestion is detected.
- After congestion is detected, the window size is reduced to avoid having to drop packets.
|
14. Checksum-
- Checksum is a 16 bit field used for error control.
- It verifies the integrity of data in the TCP payload.
- Sender adds CRC checksum to the checksum field before sending the data.
- Receiver rejects the data that fails the CRC check.
Also Read- CRC | Checksum
15. Urgent Pointer-
- Urgent pointer is a 16 bit field.
- It indicates how much data in the current segment counting from the first data byte is urgent.
- Urgent pointer added to the sequence number indicates the end of urgent data byte.
- This field is considered valid and evaluated only if the URG bit is set to 1.
USEFUL FORMULAS
Formula-01:
Number of urgent bytes = Urgent pointer + 1
Formula-02:
End of urgent byte
= Sequence number of the first byte in the segment + Urgent pointer
|
16. Options-
- Options field is used for several purposes.
- The size of options field vary from 0 bytes to 40 bytes.
Options field is generally used for the following purposes-
- Time stamp
- Window size extension
- Parameter negotiation
- Padding
A. Time Stamp-
When wrap around time is less than life time of a segment,
- Multiple segments having the same sequence number may appear at the receiver side.
- This makes it difficult for the receiver to identify the correct segment.
- If time stamp is used, it marks the age of TCP segments.
- Based on the time stamp, receiver can identify the correct segment.
B. Window Size Extension-
- Options field may be used to represent a window size greater than 16 bits.
- Using window size field of TCP header, window size of only 16 bits can be represented.
- If the receiver wants to receive more data, it can advertise its greater window size using this field.
- The extra bits are then appended in Options field.
C. Parameter Negotiation-
Options field is used for parameters negotiation.
Example- During connection establishment,
- Both sender and receiver have to specify their maximum segment size.
- To specify maximum segment size, there is no special field.
- So, they specify their maximum segment size using this field and negotiates.
D. Padding-
- Addition of dummy data to fill up unused space in the transmission unit and make it conform to the standard size is called as padding.
- Options field is used for padding.
Example-
- When header length is not a multiple of 4, extra zeroes are padded in the Options field.
- By doing so, header length becomes a multiple of 4.
- If header length = 30 bytes, 2 bytes of dummy data is added to the header.
- This makes header length = 32 bytes.
- Then, the value 32 / 4 = 8 is put in the header length field.
- In worst case, 3 bytes of dummy data might have to be padded to make the header length a multiple of 4.
Also Read- IPv4 Header | UDP Header
To gain better understanding about TCP Header,
Watch this Video Lecture
Next Article- TCP Sequence Number | Wrap Around Time
Get more notes and other study material of Computer Networks.
Watch video lectures by visiting our YouTube channel LearnVidFun.