Transport Layer Protocols-
There are mainly two transport layer protocols that are used on the Internet-
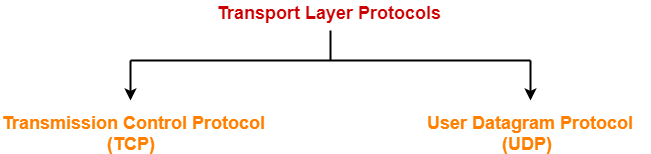
- Transmission Control Protocol (TCP)
- User Datagram Protocol (UDP)
In this article, we will discuss about Transmission Control Protocol (TCP).
Learn about User Datagram Protocol.
Transmission Control Protocol-
- TCP is short for Transmission Control Protocol.
- It is a transport layer protocol.
- It has been designed to send data packets over the Internet.
- It establishes a reliable end to end connection before sending any data.
Characteristics Of TCP-
Point-01:
| TCP is a reliable protocol. |
This is because-
- It guarantees the delivery of data packets to its correct destination.
- After receiving the data packet, receiver sends an acknowledgement to the sender.
- It tells the sender whether data packet has reached its destination safely or not.
- TCP employs retransmission to compensate for packet loss.
Read More- TCP Retransmission
Point-02:
| TCP is a connection oriented protocol. |
This is because-
- TCP establishes an end to end connection between the source and destination.
- The connection is established before exchanging the data.
- The connection is maintained until the application programs at each end finishes exchanging the data.
Point-03:
| TCP handles both congestion and flow control. |
- TCP handles congestion and flow control by controlling the window size.
- TCP reacts to congestion by reducing the sender window size.
Read More- TCP Congestion Control
Point-04:
| TCP ensures in-order delivery. |
- TCP ensures that the data packets get deliver to the destination in the same order they are sent by the sender.
- Sequence Numbers are used to coordinate which data has been transmitted and received.
Point-05:
| TCP connections are full duplex. |
- TCP connection allows to send data in both the directions at the same time.
- So, TCP connections are Full Duplex.
Point-06:
| TCP works in collaboration with Internet Protocol. |
- A TCP connection is uniquely identified by using-
Combination of port numbers and IP Addresses of sender and receiver.
- IP Addresses indicate which systems are communicating.
- Port numbers indicate which end to end sockets are communicating.
- Port numbers are contained in the TCP header and IP Addresses are contained in the IP header.
- TCP segments are encapsulated into an IP datagram.
- So, TCP header immediately follows the IP header during transmission.
Point-07:
| TCP can use both selective & cumulative acknowledgements. |
- TCP uses a combination of Selective Repeat and Go back N protocols.
- In TCP, sender window size = receiver window size.
- In TCP, out of order packets are accepted by the receiver.
- When receiver receives an out of order packet, it accepts that packet but sends an acknowledgement for the expected packet.
- Receiver may choose to send independent acknowledgements or cumulative acknowledgement.
- To sum up, TCP is a combination of 75% SR protocol and 25% Go back N protocol.
Point-08:
| TCP is a byte stream protocol. |
- Application layer sends data to the transport layer without any limitation.
- TCP divides the data into chunks where each chunk is a collection of bytes.
- Then, it creates a TCP segment by adding IP header to the data chunk.
- TCP segment = TCP header + Data chunk.
Point-09:
| TCP provides error checking & recovery mechanism. |
TCP provides error checking and recovery using three simple techniques-
- Checksum
- Acknowledgement
- Retransmission
Also Read- Checksum
To gain better understanding about Transmission Control Protocol,
Next Article- TCP Header
Get more notes and other study material of Computer Networks.
Watch video lectures by visiting our YouTube channel LearnVidFun.